Ransomware Guide 101: What to Expect and How to Respond
June 27, 2023
Ransomware and cyber attacks are becoming pervasive threats that are targeting large and small businesses alike.
Every type of organization and industry should be taking action to safeguard their data from ransomware, using best practice tips and guidelines to help keep safe and protected.
Below we take a closer look at what ransomware is, how ransomware attacks typically work, common cybersecurity threats to watch out for, and at tips to enhance your ransomware defenses.
The implications of this type of malware on any system can be devastating - often crippling businesses altogether. That’s why it's best to take a proactive stance and get started with
improving your cybersecurity so that you don’t fall victim to a costly and stressful ransomware attack.

What is ransomware?
Ransomware is a type of malware that is used to encrypt your data and make it irretrievable so that you are pressured into paying a ransom for its safe return.
Ransomware attackers usually threaten to either destroy or expose your data unless you pay their ransom demands (usually in untraceable cryptocurrencies like Bitcoin). These ransom demands can be over USD$1 million. And even if you do end up paying, there’s no guarantee they will honor that agreement - they are after all cybercriminals.
Ransomware can affect just one computer or many computers on a shared network. The effects of a ransomware attack can be devastating and stressful for all involved. Without access to their data, companies may not be able to operate at all. And if their data is breached, that also has serious privacy and data security implications. Business disruptions like this can have serious financial, legal, reputational and even personal safety implications.
Unfortunately the
prevalence of ransomware attacks is on the rise. And as part of these attacks, cybercriminals may also target your backups, to pressure you into paying the ransom.

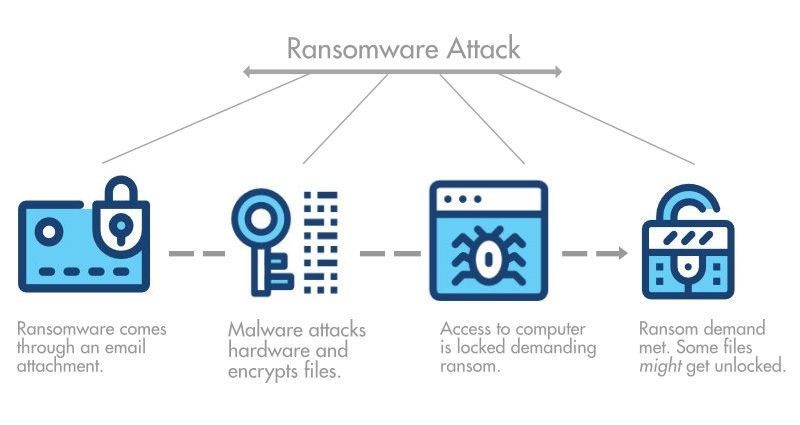
How does a ransomware attack work: what to expect
A ransomware attack usually happens in phases.
First a cybercriminal needs to gain access to a computer or system. This is typically done by getting a user to run a program that contains
malware (often through a
phishing scam that gets you to click a link in an email or even via sms) or by stealing your login credentials.
Next, the cyber attacker will try to encrypt or destroy your files and your backups - and may need to find the highest permissions possible to access as much of your system as possible.
Finally, the cybercriminal behind the ransomware attack will try to complete the hack by encrypting or deleting your files and sending you a message to contact them via email about getting your data back in exchange for ransom.
If your business has cybersecurity measures in place to detect a ransomware attack, your IT team or MSP could then identify the threat and act quickly in line with established protocols to retrieve, recover and restore data so that your business can continue operating.
Cybersecurity threats to watch out for
To safeguard against ransomware attacks, it’s good to know what type of cybersecurity threats to watch out for.
Below are some of the most common types of ransomware threats (or infection vectors) to look out for:
1. Email phishing
Most ransomware attacks are a result of email phishing. This is when you are either fooled into providing your personal details in response to an email, or when you respond to an email from someone trusted whose credentials have been compromised and taken over by a hacker.
2. Malicious links
Another vector for spreading malware is when you receive an email or visit a website or social media site that contains malicious links. When you click on that link, your device may then get infected with malware. That includes ‘malvertising’ where you see an enticing advert to download some free software, which turns out to actually be malware.
3. Remote desktop protocol access
Ransomware attacks are a growing concern for businesses and individuals alike. One common method of spreading ransomware is through remote desktop access.
In this type of attack, an attacker gains access to a victim's computer via remote desktop protocol (RDP) and then uses that access to install and execute the ransomware.
An example of such an attack is the
Ryuk ransomware attack, which targeted several large organizations, including the city of New Orleans. The attackers used RDP to gain access to the city's network and then spread the ransomware throughout the network, disrupting city services and causing significant financial losses.
This highlights the importance of implementing strong security measures for remote desktop access and regularly updating and patching systems to prevent similar attacks from happening.
Top tips to avoid a ransomware attack and stay protected
Below is a curated list of top tips to help you avoid a ransomware attack.
Use Multi-Factor Authentication (MFA)
Employing the use of multi-factor authentication (MFA) across all your user accounts and devices helps to add a layer of extra security against cyber intrusions. That includes using MFA for email logins, for cloud service logins, for social media logins, and for any critical IT technologies.
Use strong passwords
Having a password policy and establishing strong username and password protocols can also help to protect against ransomware.
Follow the 3-2-1 backup rule
Having backups of all your data and information is critical to being able to remain unaffected by ransomware attacks. But because attackers may target your backups, it’s good to follow the 3-2-1 rule and have at least one copy of your data stored offline and off-premise.
Take an inventory of all your data
Take an inventory of all your data and where it is stored, categorizing it into critical and least critical data so you know what to restore with priority should your data be affected. That includes keeping an updated network diagram.
Test for vulnerabilities
It’s important to test your system continuously for vulnerabilities and gaps that can then be patched and secured. This helps to build data security.
Have a disaster recovery plan
Having a disaster recovery plan is critical to ensure your business recovers quickly from a cyber attack and that your team knows what to do and what protocols to follow to lessen the impact and respond to any breaches.

Keep your antivirus software and other applications updated
Professional antivirus software can also add a layer of useful protection that can identify and eliminate threats before they become a problem. Ensure that your antivirus software is kept updated, and that your other software, firmware and operating system is also up-to-date.
Also remember to consider security for all your endpoints including laptops, mobile phones, VoIP phones, servers and desktop computers.
Conduct regular cybersecurity awareness training with staff
Given that most ransomware is spread through email phishing scams, training your staff regularly on how to identify scams and suspicious emails can have a significant impact.
Organizations can also conduct
cybersecurity training exercises to see if staff are able to actually detect a phishing scam, and to reinforce what’s been learned in awareness training programs.
Training can also help staff to
recognise the signs that their computers may be infected, such as strange popups or new sluggish behavior.
Limit access and privileges
Not every employee needs access to all your data. You can limit access to data and privileges to help protect data from being accessed in the event of a ransomware attack.
Regularly audit all your users to see what privileges they have and need, and to ensure they don’t have privileges they shouldn’t. That includes auditing privileges given to MSPs and third party suppliers and vendors. It’s particularly important to review any administrative access privileges.
Segment your network
By segmenting data on your network, you can help to protect and isolate areas of your network from ransomware attacks. That can be done using a network of firewalls.
Switch to cloud email
Switching from legacy and on-premise emails to cloud email systems can also help to safeguard your data security. That’s because most reputable cloud email providers have the latest security protocols to monitor and protect against ransomware.
Guide on how to respond to a ransomware attack
The best way to respond to a ransomware attack is to be prepared and have a well thought out plan of how to handle every situation. Time is of the essence when your security defenses have been breached, so having a disaster recovery plan in place can help you to minimize the damage. If every staff member knows what their role is and how to deal with different types of scenarios, the process should run more smoothly.

Once you have a disaster recovery plan in place, it’s also important to continuously monitor and identify threats.
If a threat is detected, your team needs to act quickly to contain the threat by patching the entry point and then removing the threat altogether before restoring all data. You may also need to reset passwords, wipe infected devices, and reinstall software before getting back to being operational.
Need help to safeguard your business against ransomware?
NB Technology is your go-to for safeguarding your business against ransomware attacks. Our experts will work with you to fortify your cybersecurity, detect and respond to potential threats, secure all your endpoints, and provide additional layers of protection through cloud-based solutions and data backups. Our disaster recovery plans ensure that your business can continue to operate even in the face of an attack.
Contact us at (704) 644-1220 for a no obligation consultation to discuss your
cybersecurity needs and any inquiries you may have.











